Connected Cars adheres to industry-leading IT standards and is fully compliant with the EU’s General Data Protection Regulation (GDPR). Our company has been rigorously audited and certified under the TISAX standard, among others, demonstrating our commitment to the highest standards of data security in the automotive industry. This commitment extends from the CC-Link device all the way to our customer frontends, ensuring comprehensive protection at every level.

At Connected Cars, we prioritize your security and privacy by adhering to the highest industry standards:
Our information security management system is certified against the TISAX standard (Trusted Information Security Assessment Exchange), developed by the German automotive industry.
This certification, conducted by Bureau Veritas, ensures a consistent level of information security among its suppliers. We are proud to present our stellar assessment results, which are publicly available on the TISAX platform (Assessment ID: AV66AK-1).
In alignment with VDA’s ISA version 5, our practices incorporate controls from various ISO standards including ISO 27001:2013 and ISO 27017. These standards help us build a robust information security management system with special relevance in the automotive industry.
We implement organizational and technical security measures based on the CIS Critical Security Controls, which are a prioritized set of safeguards to mitigate the most prevalent cyber-attacks. This approach is designed to fit both American and European security standards, ensuring comprehensive protection for our automotive services.
Our development processes are guided by the principles of the Open Worldwide Application Security Project (OWASP), ensuring that we follow the latest security procedures and best practices to protect your data.
At Connected Cars, we go beyond the standard requirements to ensure a secure and reliable experience for our users. Here are some of the additional measures we have in place:
Connected Cars conducts an independent penetration test annually on our web applications and APIs. The latest tests have found no critical vulnerabilities, and all minor issues were promptly addressed and resolved. This reaffirms our security standing in the market and our commitment to high-level IT security maturity.
We have established a comprehensive ISMS, detailed in our Information Security Policy and Rules Handbook. This system is primarily focused on maintaining rigorous security controls through recurring security tests and assessments. These continual evaluations ensure that our security measures are consistently effective and aligned with the latest security standards and threats.
In our recent patent due diligence, conducted by the company Inspicos, no granted patent rights were found that conflict with or are infringed by Connected Cars products. This evaluation ensures that we operate freely without infringing on existing patents.
A thorough review by Horton confirmed that our operations, including agreements with employees, consultants, and subcontractors, do not pose any significant legal or operational risks related to intellectual property.
We adhere to the UNECE WP.29 regulations, as outlined in the ECE/TRANS/WP.29/2020/79 Revised document. This includes a comprehensive review of threats and mitigations applicable to vehicle manufacturers. Our ISMS checks and procedures are robust, fully addressing these regulations and supporting compliance towards original equipment manufacturers (OEMs).
At Connected Cars, your data remains secure from prying eyes. Our robust encryption protocols and meticulous privacy measures guarantee that your sensitive information stays confidential every step of the way.
Connected Cars is 100% compliant with the EU’s General Data Protection Regulation (GDPR) and ensures adherence to privacy regulations in other international markets to serve our broad global customer base.
As Connected Cars is located in Denmark and thus subject to GDPR, we operate in accordance with the legislation. In this regard, Connected Cars adheres to, among other things, the fundamental principles, respects the rights of the data subjects, and provides sufficient data processing security.
Another major change imposed by the GDPR is audit logging. To ensure that Connected Cars and our customers are compliant with the regulation, our systems keep track of who (users, admins, operators) views and edits data. Unsuccessful user login attempts are also logged. Audit logs are stored for 5 years in a secure location with restricted access.
We ensure compliance with both local and international regulations. By engaging specialized lawyers, we align our data protection and information security practices with the varying legal frameworks across the markets we serve, guaranteeing robust and effective compliance globally.
Users can be confident that their personal data has been handled in accordance with GDPR principles of privacy by design and the right to be forgotten. The right to be forgotten is a main pillar of GDPR. This principle, which makes it possible to identify the location of personal data—either all company data or individual user data—and to delete or anonymize it, is incorporated into all systems and processes.
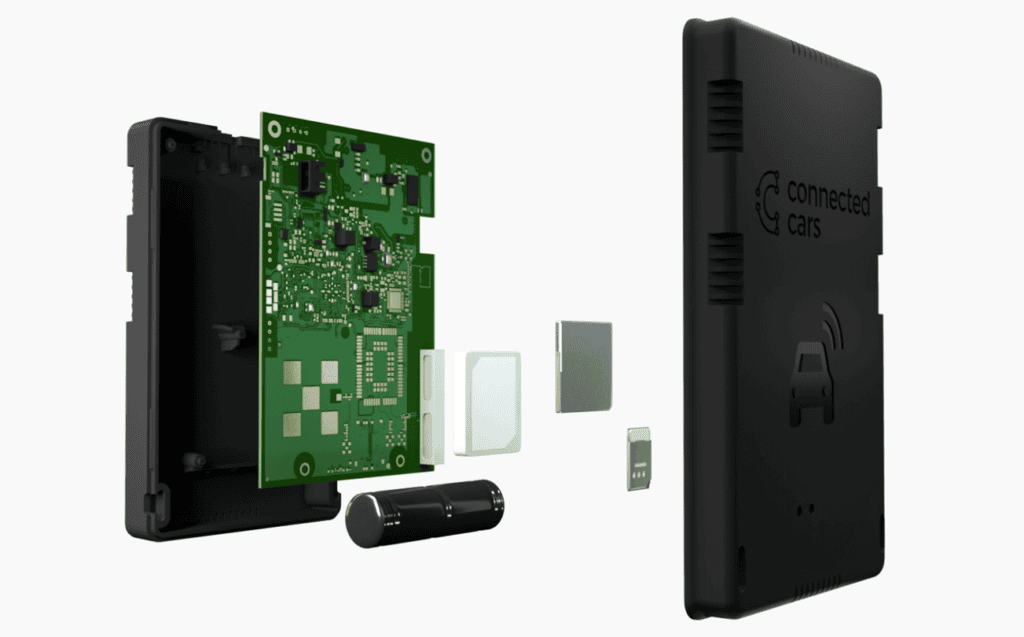
We have developed a cutting-edge telematics unit, CC-Link, designed to seamlessly gather vehicle data. This device is produced at ISO 9001 certified factories and is discreetly installed behind the dashboard, interfacing directly with the vehicle’s OBD-II diagnostics socket.
The data captured by CC-Link is securely transmitted to the Connected Cars cloud and made accessible to end-users via a mobile app, and to workshops and fleets through a web application, all while strictly adhering to user consents.
Our firmware undergoes a rigorous validation process, including peer reviews by our internal teams, comprehensive in-house and on-road testing in test vehicles, and thorough security assessments. The integrity of the firmware is consistently verified through advanced hashing functions. We are committed to regular firmware updates to enhance functionality and security.
Our system components are meticulously hardened, and our software images are optimized to contain only the essential elements. Notably, Connected Cars operates without any on-premise servers; all access to our cloud-based infrastructure is tightly controlled through role-specific credentials and robust two-factor authentication, requiring renewal every 12 hours.

For a deeper understanding of our security measures, we provide access to various TISAX-assessed and externally validated documents upon request. Please contact us to inquire about these resources, and we will assist you with the necessary information.
Depending on the country and the relationship to GDPR, the legal framework describing the handling of personal data includes a section on the organizational measures we take to ensure a high level of security. These sections are:
– Data Processing Agreement (DPA) section “C2. Security of Processing”
– Standard Contractual Clauses (SCC) section “Annex II – Technical and organizational measures including technical and organizational measures to ensure the security of the data”
If you discover a security vulnerability, encounter a potential bug, or have concerns related to the security of our services, we encourage you to report it responsibly. You can reach our security team directly at security@connectedcars.io. We value such contributions as they help us maintain a high level of safety and trust for all our users.
We are dedicated to transparency and give you complete control over how your data is used. Experience the peace of mind that comes with unparalleled security and compliance.